The WordPress HTTPS Mixed Content Detector Plugin - What All it Entails
WordPress accounts for close to 25% of the total number of websites on the World Wide Web. The figure, by any measure, is staggering.
With the exceptional set of features and capabilities that are unique to WordPress, its ever growing popularity is hardly any surprise. However, as with any massively popular entity, WordPress draws a lot of prying eyes from those with malicious intentions. Hackers always have WordPress websites as their prime targets, and unsurprisingly so. And to put it quite frankly, there are loopholes for them to explore.
A typical WordPress-based website contains features installed not just via the default setup, but also via plugins, the basic theme and other sources. So, there is not a single, authorized source that is feeding a WordPress website. There are multiple third party sources, and that’s where the security threats emanate from.
When you are running a TLS enabled website, you need to be extra cautious and be certain that all the content loaded on the site is coming from a trusted and secure source. As a result of the security threats, the web browsers may also start giving out the mixed content issue, or in worse case scenario, block the website altogether.
Now, to deal precisely with such an issue, we have a handful of plugins out which, the HTTPS Mixed Content Detector unarguably comes across as the best. This plugin does the task of identifying all the origins of the mixed content warnings.
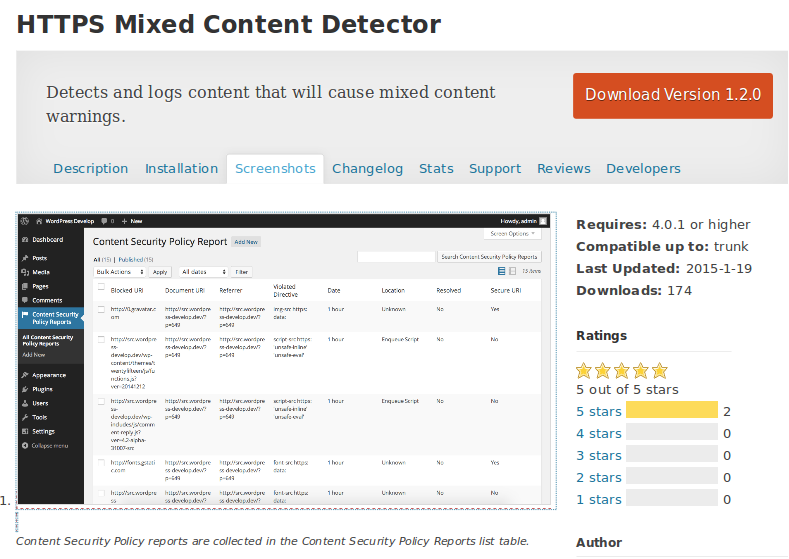
The HTTPS Mixed Content Detector plugin can easily searched and installed, and once that is done, as an admin, you can see various options appearing the dashboard. All the unsecured assets are generated as a part of the list and you can examine all these assets closely. Following that, you can replace the unsecured assets with the secure ones.
There is a straightforward way to how this plugin works basically. When the admin of the site is loading the site, the plugin starts logging the nonsecure items. Carefully analyzing the log will help you gain an in-depth insight into what’s causing the errors from showing up and how you can deal with all the warnings.
How HTTPS Mixed Content Detector Plugin Works
At the very core of the HTTPS Mixed Content Detector plugin is the Content-Security-Policy-Report-Only header. This header performs the job of detecting the assets coming from authentic or suspicious sources. So, when the asset from a suspicious source does drop in, the header generates an alert by setting a report only content policy. Or, you can set a report-uri through the header that will perform the job of notifying you every time suspicious content encountered. With our plugin, a special URL represents this notification sent to you, and it is sent to you at every instance of the content violation. As the URL gets pinged, the logging of content violation will take place. And this log can be viewed as and when you get time to do so. As the Content-Security-Policy-Report-Only header is already in place, the diverse items will be allowed the entry unless the browser settings block out the assets which are already logged. And among those items, those that are unsecure will be promptly detected and you will be notified about the same. Even before the TLS is implemented on the site, the deployment of this plugin will take place. And therefore, it ensures that all the security threatening items are promptly identified and dealt with before they go on t affect the website’s performance in any negative manner.
What Part Does the Content Security Policy Play
To begin with, all the assets coming in from resources like “http://”, instead of “https://” are taken to be as security risks. Now, this is not a failsafe way to ensure security since not all security-threatening assets are logged.
This is where the Content Security Policy comes into play as it creates a shield around the wall to keep the vulnerabilities at bay. It is the browser that is responsible for monitoring the content and log the content that violates the security parameters.
You must keep it in mind that it’s not only the risk of losing your data that should compel you to protect your site, but it is also the fear of search engines penalizing you for your more than apparent security threats that should really make you sit up and take notice.
About the Author:
A seasoned web developer, Amanda Cline has extended her expertise to blogging as she writes elaborate and insightful articles around various pertinent web technologies. If you need to hire PHP developer then simply get in touch with Amanda via Twitter or Facebook. Currently, she is working with Xicom Technologies Ltd – offshore web development Company.
Please let us know your comments and suggestions: